Don’t be so reckless as to rush to removing passwords
![“Expanded Password System
wane = Only I can select all of
BS] them correctly
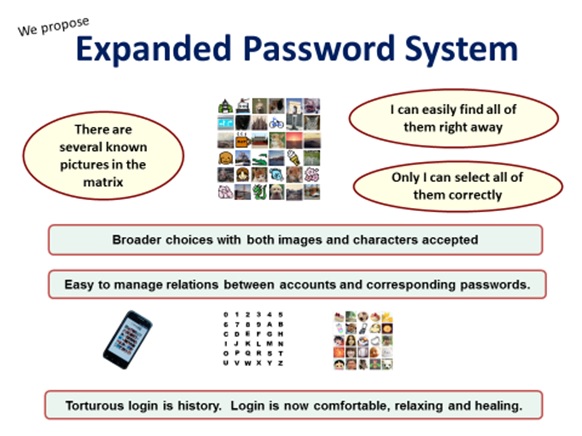
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/don-t-be-so-reckless-9KKSWb0Da1Ak/jN5gw.png)
“US House Rep on cyber committees tweets Gmail password, PIN in Capitol riot lawsuit outrage” https://www.theregister.com/2021/06/07/brooks_gmail_password/
It says “Brooks, who sits on the House's Cyber, Innovative Technologies, and Information Systems subcommittee, and the Science, Space, and Technology committee, tweeted a photo from an iPad of his Windows computer, attached to which was a piece of paper with login credentials written on it.”
Being vulnerable to abuse does not mean being detrimental, just as an army vulnerable to air strike is not detrimental.

Removing the password altogether would only destroy identity security, just as the removal of an army would destroy national defense.
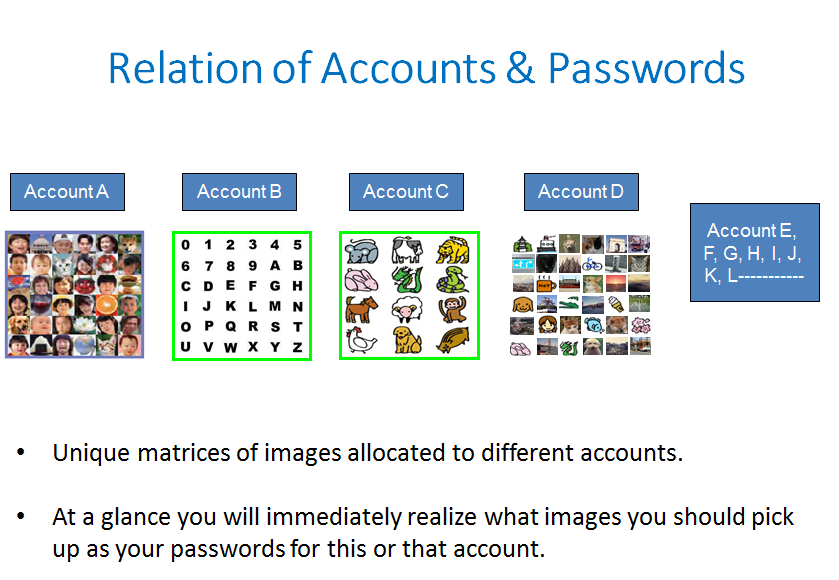
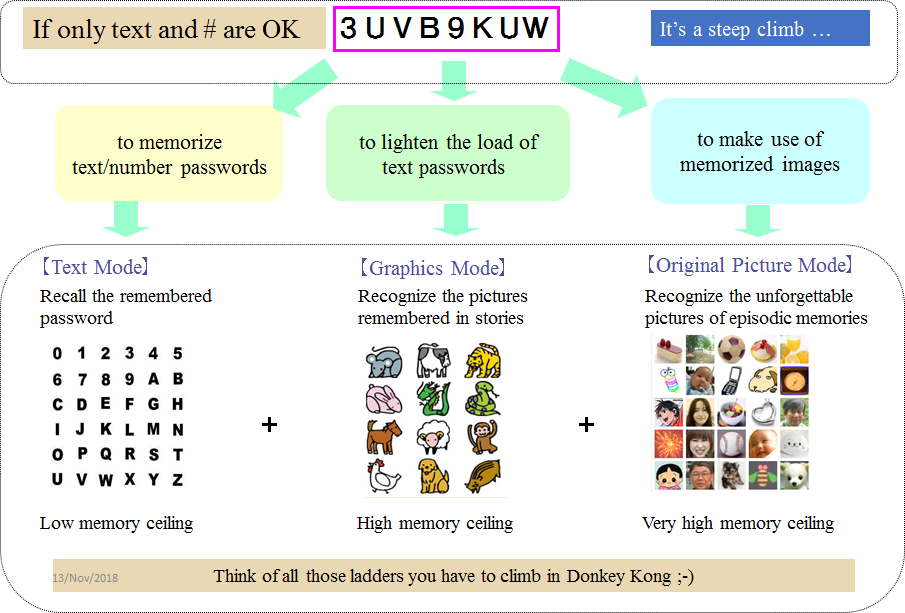
The password headache could be mitigated if our passwords to be fed for login are made of two components – one half to recall and the other half to recover from a memo or device.
This is actually what I am practicing for feeding 200-bit strong passwords every day at present, that is, until our leak-free password manager is put on the market.
By the way, you would quickly realize what the leak-proof password manager will be like if you try and experience the flow of image-to-code conversion at our new website - https://www.mnemonicidentitysolutions.com/
Key References
Account Recovery with Expanded Password System
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Additional References
Removal of Passwords and Its Security Effect
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Articles from Hitoshi Kokumai
View blog
The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intellige ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
We today take up this report “NSA: We 'don't know when or even if' a quantum computer will ever be a ...
Related professionals
You may be interested in these jobs
-
Junior Video Editor
Found in: Talent UK C2 - 12 hours ago
Student Beans London, United Kingdom Full timeAs a result of our incredible success and growth within our Social and Content team, we are looking for a brand new Junior Video Editor to join us You'll be working alongside a team of 3 within the Video production team, who work collaboratively with our channel specific teams to ...
-

Dynamics CRM Lead Consultant
Found in: Jooble UK O C2 - 4 days ago
Odevo AB London, United KingdomOdevo is a group of exciting brands with a shared vision of challenging the status quo in the property management industry. We're committed to revolutionizing the industry with innovative software solutions that make managing properties easier, more efficient, and more effective. ...
-
Preceptorship / Newly Qualified Nurse - RMN / RNLD
Found in: Indeed UK C2 - 11 hours ago
Appoint Healthcare York, United Kingdom Full timeSalary: £32k per year · Reference: 58994 · Preceptorship / Newly Qualified Nurse · Location: Clifton, York · Salary: £32,000 per annum + £1,500 welcome bonus · Hours: Full Time Preceptorship Programme · Company / Service information: · An exciting opportunity has arisen for an Pr ...



Comments
Zacharias 🐝 Voulgaris
2 years ago #3
Couldn't agree more, my friend!
Hitoshi Kokumai
2 years ago #2
Perhaps it is why many cryptographers are trying to not think about the human side of identity authentication for which mathematics is not almighty.
Zacharias 🐝 Voulgaris
2 years ago #1
It's funny how we have the most sophisticated confidentiality methods the world has ever seen (from encryption to steganography, to various combinations of the two, as well as fully homomorphic encryption), yet we still haven't mastered the habit of proper password usage and management. It's really fascinating how Authentication still remains the most relevant part of Cryptography, even today after it's matured to levels previously considered unfathomable. Cheers