Leak-resistant Secret Credentials
![“Expanded Password System
wane = Only I can select all of
BS] them correctly
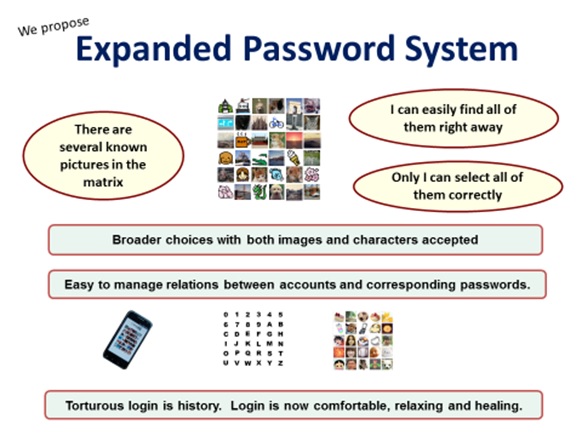
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/leak-resistant-secret-credentials-S0UEKjhfyUpD/LJhNK.png)
Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of credentials” https://www.theregister.com/2021/09/22/microsoft_exchange_autodiscover_protocol_found/
It appears to be next to impossible for any talented servicers to locate all the critical vulnerabilities before someone else, bad guys in many cases, locate them. Then we should better assume that our own credentials could leak at any time.
One of the valid solutions against it would be to use the passwords whose hashed entropy is so big as to stand the brute force attacks by supercomputers. It is not what humans can easily do, however, meaning that we need a powerful tool to achieve it like the stones and clubs for our ancestors.
Our proposition of ‘image-to-code conversion’ might well make a sizeable contribution as discussed here “New Slide - Healthy Second Life of Legacy Password Systems” https://www.linkedin.com/posts/hitoshikokumai_bring-a-healthy-second-life-to-legacy-password-activity-6837948929376681984-xKjH
Well, were you considering that killing the password could be a solution?
What does not exist will indeed not leak, but we will end up seeing our future killed; Where our identity is established without our will/volition confirmed, democracy is fatally eroded. Practically we would no longer have a restful sleep unless staying alone in a closed space locked from within or fenced by faithful bodyguards.
Incidentally, the security effect of removing the password is discussed here – “Remove the army and we will have a stronger national defense”
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08">
Key References
Bring a healthy second life to legacy password systems
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
Memories
Episodic Memory">
Additional References
Removal of Passwords and Its Security Effect
Step-by-Step Analysis of Why and How Biometrics Brings Down Security
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
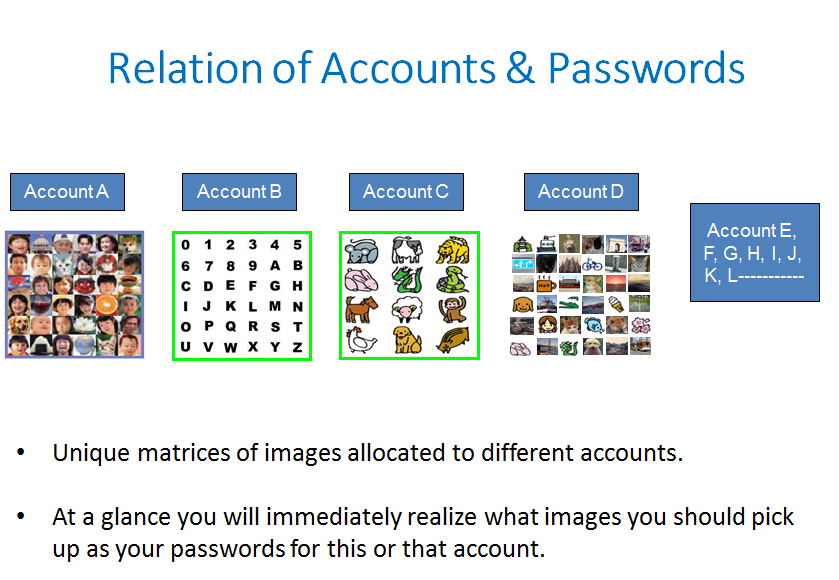
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.">
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Articles from Hitoshi Kokumai
View blog
https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...

Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...
You may be interested in these jobs
-
Regional Sales Manager
Found in: Talent UK C2 - 1 day ago
Spark Innovations London, United Kingdom Full timeThis role offers a unique opportunity for career growth and development within our sales department. The successful candidate will undergo comprehensive training for one month, learning the ins and outs of our products/services and mastering face-to-face sales techniques. After t ...
-
Bricklayers (Contract, Temporary)
Found in: Jooble UK O C2 - 6 days ago
Mango Solutions Recruitment Ltd Milton Keynes, Buckinghamshire, United KingdomWe are Looking for Brickleyer for Milton Keynes · Description · Monday to Friday on going. · bricklayer / grounds worker able to build, set out and form concrete ramps for access to properties, small masonry repairs and hand dig, install drainage gullies, mix and float concrete. ...
-

Homeworking Sales Advisor
Found in: Jooble UK O C2 - 5 days ago
Shutterstock, Inc London, United KingdomCommercial Sales Operations & Analytics Associate page is loaded Commercial Sales Operations & Analytics Associate · Apply locations London time type Full time posted on Posted 2 Days Ago job requisition id R About The Opportunity · Shutterstock is a leading global creative pla ...

Comments