Nonpredictable Passwords Carried Around on Memo
I got interested in this article -on the password problem “Tech Q&A” https://www.unionleader.com/nh/lifestyles/tech-q-a-safeguarding-against-password-hackers/article_16d3629e-b5ba-550b-b2ac-6070403f61a4.html
Their answer is “The best defense against brute force and dictionary attacks is to use a password that is a long combination of letters, numbers and symbols that would be meaningless to anyone but you. These so-called “nonpredictable passwords” are far more difficult to hack.”
It would be fine for you if you are confident you are always able to recall all of them along with the correspondence with all the accounts to use these passwords for under any circumstances. Then, you would not have to carry around a memo on which all the accounts and corresponding passwords are written down; the memo would work as a single point of failures and vulnerabilities.
Should you be not so certain about your such ability, you might be interested in our password discussions such as “Dual Causes of Password Predicament”
and “Password Manager or Expanded Password System”
![“Expanded Password System
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/nonpredictable-passwords-carried-around-on-smRivS114GBH/GDtq2.jpeg)
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
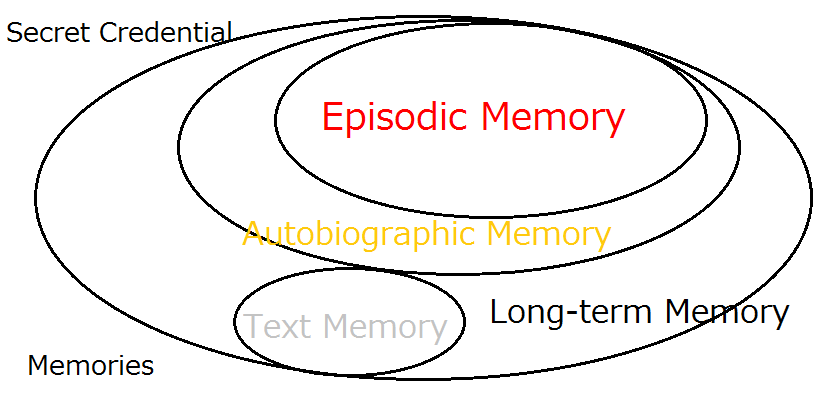
08Secret Credenti
Memories
Episodic Memory">
Key References
Bring a healthy second life to legacy password systems
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
Memories
Episodic MemoryDED
RDaDHP
BOP v6
mec Ne
gr |ar
Generating High-
Entropy Password like
xtyax9d4294dlelEYVz
wo/gadieowUx093/x7
?lwble84x09xloPxLxeo
dtyYDidex&&xeigo@y...">
Additional References
Removal of Passwords and Its Security Effect
Step-by-Step Analysis of Why and How Biometrics Brings Down Security
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
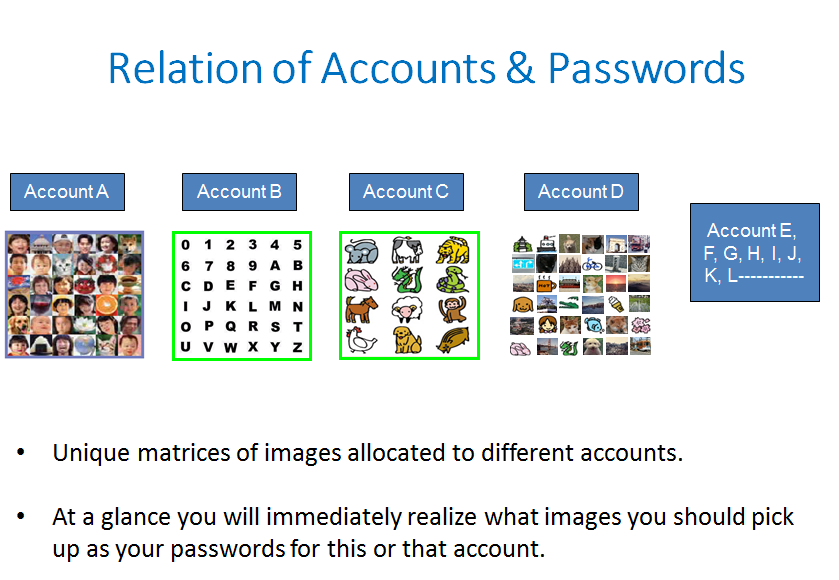
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.Relation of Accounts & Passwords
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.">
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
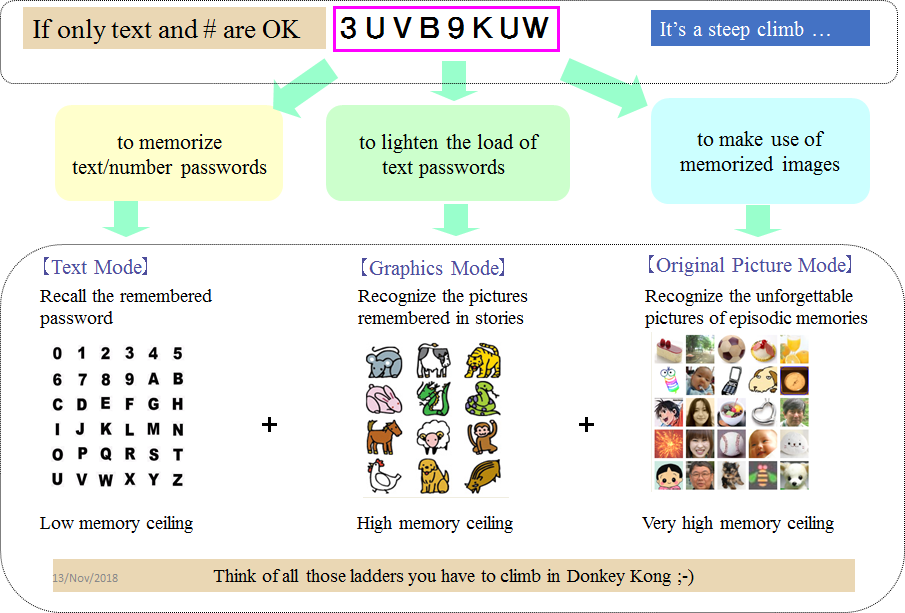
to memonze
text/number passwords
{Text Mode)
Recall the remembered
password
J 2
co-o0o
Ox ma
XxXBFr mow
a
NAzZZIoaw
+
Low memory ceiling
to lighten the load of
text passwords
{Graphics Mode)
Recognize the pictures
remembered mn stones
High memory ceiling
[RE RET RSI
to make use of
memorized images
{Ongimal Picture Mode)
Recognize the unforgettable
pictures of episodic memories
sRBO yr
L@ S00
afson
fa
Very high memory cuiding
— Think ofall those adders you have to climb in Donkey Kong 1+)">
Articles from Hitoshi Kokumai
View blog
Bad guys, who have a quantum computer at hand, would still have to break the part of user authentica ...
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...

I today take up this The Register report - “Client-side content scanning as an unworkable, insecure ...
Related professionals
You may be interested in these jobs
-
Sales Operator
Found in: Talent UK C2 - 1 day ago
Europa Worldwide Group Sheffield, United KingdomPosition Summary: · To support the Account Manager through administrative duties to allow them to focus on new and existing business development. Along with general office admin this will also involve the direct communication with their customer base via email and phone, along w ...
-
Electrical and Electronic Engineering Graduate Programme
Found in: Talent UK C2 - 1 week ago
Babcock International Group Rosyth, United KingdomElectrical and Electronic Engineering Graduate Programme · Salary: £32,* · *Minimum £32,. Salary is dependent on location, role and qualifications. · Location: Rosyth, Scotland · Application closing date: 8 May · Programme start date: Autumn · About the programme · Electrical ...
-

finance manager
Found in: SonicJobs Direct Apply UK - 4 days ago
Direct apply
Forrest Recruitment Liverpool, United Kingdom Full timeFINANCE MANAGER, Wavertree Based. · £17.58 per hour, weekly pay. · Immediate start, 2 month + duration. · Mon to Fri, Hybrid (2 office based, 3 home). · Responsibilities: · Ensuring accurate financial records and accounts are maintained and performance monitored against company ...

Comments