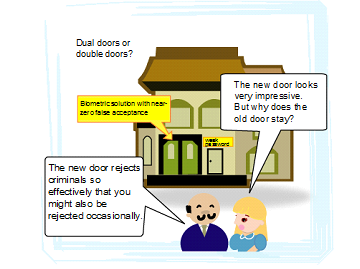
So, what should we do when we see a correct user falsely rejected?

Today's topic is this report “Thales launches payment card with onboard fingerprint scanner” https://www.theregister.com/2021/07/22/thales_fingerprint_payment/
Is the user expected to give up the payment opportunity altogether or is expected to feed the default password as a fallback measure?
Alleging ‘improved usability’ would be misleading in the former case, whereas alleging ‘improved security’ would be misleading in the latter case.
As such, what they claim is false.
More of our reasoning is offered here – “Negative Security Effect of Biometrics Deployed in Cyberspace”
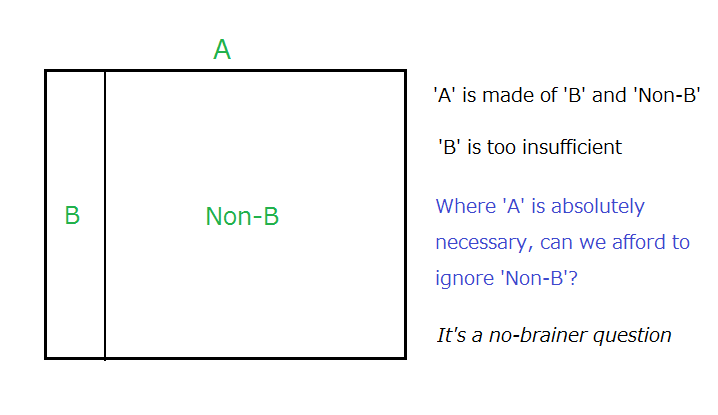
Incidentally, a nice figure is quoted as False Acceptance Rate, but such a figure makes no sense unless it comes with the empirical False Rejection Rate that corresponds to the said False Acceptance Rate; these two rates are in the trade-off.

Key References
“What we need to do for NOT achieving Solid Digital Identity”
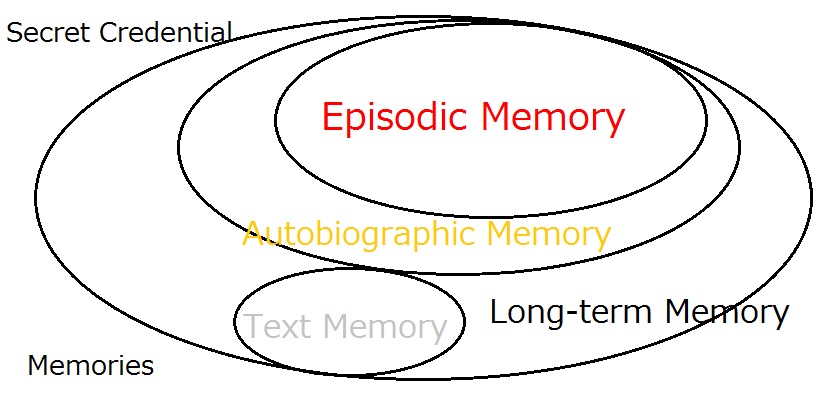
Removal of Passwords and Its Security Effect
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’

Additional References
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Articles from Hitoshi Kokumai
View blog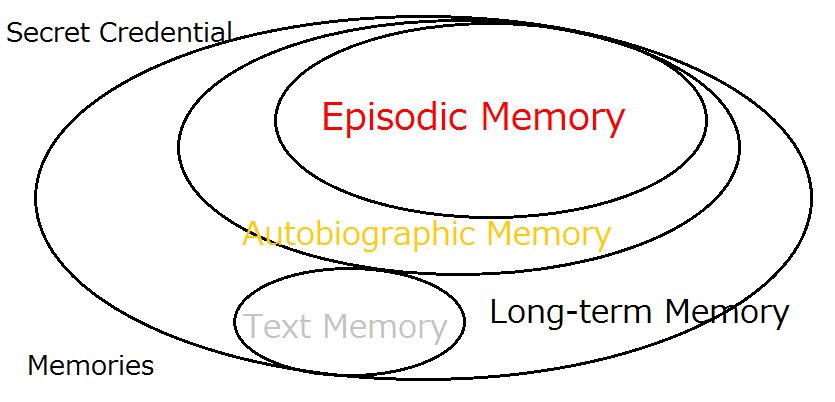
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...

Bad guys, who have a quantum computer at hand, would still have to break the part of user authentica ...
There is actually a valid methodology that enable us to maximize the entropy of the secret credentia ...
Related professionals
You may be interested in these jobs
-

German to English speaking Translator
Found in: Jooble UK O C2 - 5 days ago
Euro London Appointments Milton Keynes, Buckinghamshire, United KingdomJob Title: German to English Translator (office based) Location: Milton Keynes, UK (hybrid basis) · Type: Full-time · Salary: £28,000 - £32,000 per annum (depending on experience) · Are you fluent in German and motivated to use it professionally? Do you have a passion for trans ...
-
HR Procurement Manager
Found in: Jooble UK O C2 - 1 week ago
1st Executive Oxford, Oxfordshire, United KingdomRole: Procurement Manager - IT, HR & Corporate Services · Hybrid: Ideally 2 days office, 3 days WFH · Excellent opportunity to join a fantastic corporation that is continuing to expand and offers brilliant progression opportunities to the right candidate. You'd be joining an ag ...
-

Test Engineer
Found in: Jooble UK O C2 - 1 week ago
Continental Engineering Services Gesellschaft mit beschränkter Haftung United KingdomWe are currently looking for a Test Engineer to join our team at our Burgess Hill office. The successful candidates will have the opportunity to learn from our experienced team of Test Engineers. As well as being a logical thinkers, the Test Engineers should have a passion for cr ...


Comments