Solid Secret Credential for Blockchain

Today's topic is this report - “How blockchain technology can create secure digital identities” https://ibsintelligence.com/blogs/how-blockchain-technology-can-create-secure-digital-identities/
The title of this report reads “How blockchain technology can create secure digital identities”. I would have made it read “How blockchain technology, when it comes with solid secret credentials, can create secure digital identities”.
“How come?”
The lock authenticates the key and the key authenticates the lock. But neither the key nor the lock authenticates the person who holds the lock or key. It is imperative to check the secret credential of the person who claims to be the owner of the lock or key. It’s so plain and simple.
“Conventional text passwords are too hard to manage and yet too vulnerable to abuse?”
Then, why not look at non-text secret credentials?
For more, please refer to “Why the password isn’t an enemy of people”
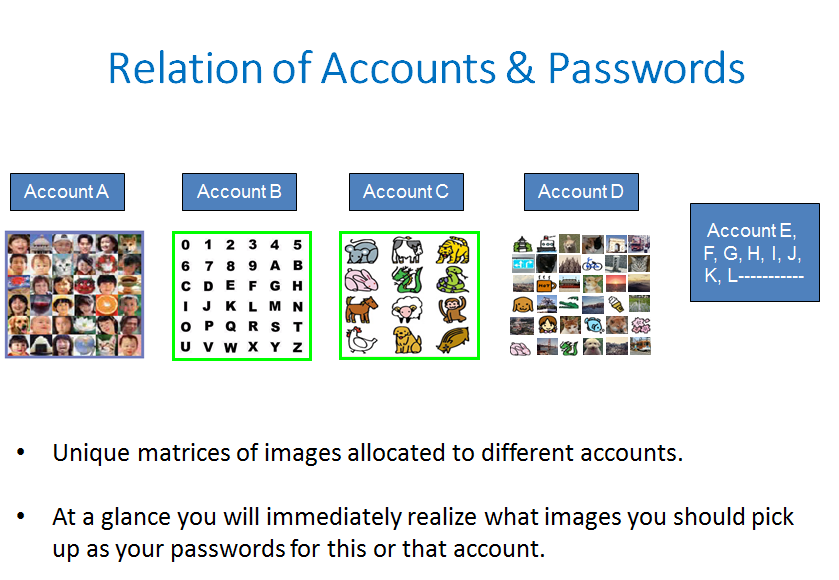
![Relation of Accounts & Passwords
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account. - “Expanded Password System
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08 - “Expanded Password System
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/solid-secret-credential-for-blockchain-vBoxq0C0ZwYv/1nAXu.jpeg)
Key References
Bring a healthy second life to legacy password systems
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
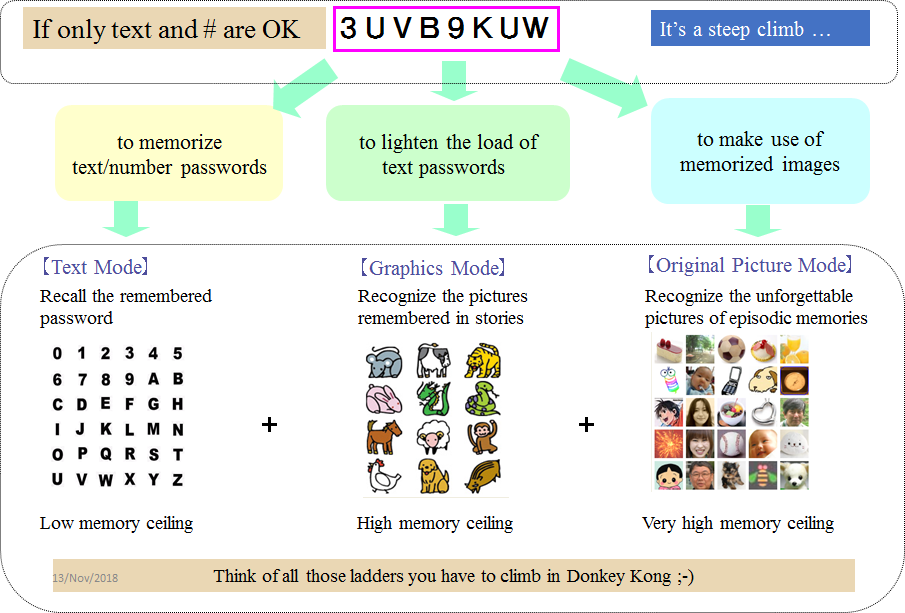
Additional References
Removal of Passwords and Its Security Effect
Step-by-Step Analysis of Why and How Biometrics Brings Down Security
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
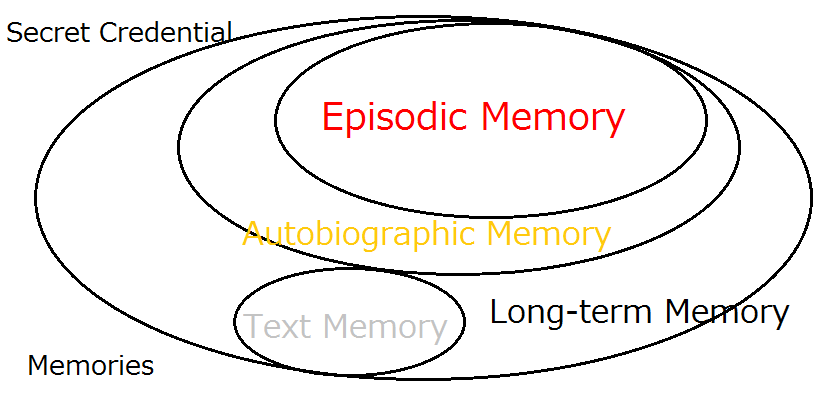
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Articles from Hitoshi Kokumai
View blog
https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...

I take up this new report today - “Researchers Defeated Advanced Facial Recognition Tech Using Makeu ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...
You may be interested in these jobs
-
Fabricator/Assembly Operative
Found in: Jooble UK O C2 - 5 days ago
Pin Point Recruitment London, United KingdomLighting Assembly Operative · Hours: Mon-Fri 8am-4pm · Our client is seeking a skilled and detail-oriented Lighting Assembly Operative to join their team in Mitcham. This is an excellent opportunity for individuals with a passion for hands-on work and a commitment to quality. · A ...
-

English Teacher Vacancy In Wandsworth
Found in: Talent UK C2 - 1 week ago
Wayman Group London, United Kingdom Full timeWayman Education is seeking a highly committed and passionate English Teacher who is keen to ignite a real passion in the students by providing a rich, varied and exciting curriculum. As a English Teacher, this role will involve you teaching as part of an established English depa ...
-
Health & Safety Coordinator (Engineered Manufacturing)
Found in: Click to Hired UK C2 - 6 days ago
GBR Recruitment Limited Thrapston, United Kingdom Permanent, Full timeGBR Recruitment Ltd are exclusively working with a leading engineered products manufacturing business based on the edge of Northamptonshire recruiting for an experienced Health & Safety Coordinator (Engineered Manufacturing processes) who is strong in HSE Administration, to help ...
Comments