Publishing by aiTech Trend

https://aitechtrend.com/quantum-computing-and-password-authentication/
My latest article titled ‘Quantum Computing and Password Authentication’ was published by NY-based aiTech Trend. https://aitechtrend.com/ Below is the gist.
-Quantum computing, however powerful, cannot place our volition and memory under its control. Conversely our volition and memory could help force quantum computing to work just for benefitting people.
-Removal of the password would bring catastrophic disasters.
-Our password headache may well be the consequence of ‘Use of Impracticable Password’ and ‘Non-Use of Practicable Password’
-It’s feasible to bring a healthy second life to legacy password systems
-We are coming up with a Password Manager powered by Expanded Password System that enables us to make use of our pleasant episodic image memory as the solid secret credentials.
-Expanded Password systems will continue to contribute to safe cyberspace even when quantum computing has destroyed the part of identity authentication that depends on public-key schemes.
By the way, what we say about Quantum Computing can also be said about Artificial Intelligence.
Assume that we (and our descendants) are put into an AI-dominated world. The last bastion that we are able to rely on for protecting us from the perils of uncontrolled AI would be our volition and memory that will continue to stay outside the realm of the AI.
Attempts to kick out our volition and memory from digital identity and identity assurance would only be insanely suicidal.
Key References
Bring a healthy second life to legacy password systems
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Account Recovery with Expanded Password System
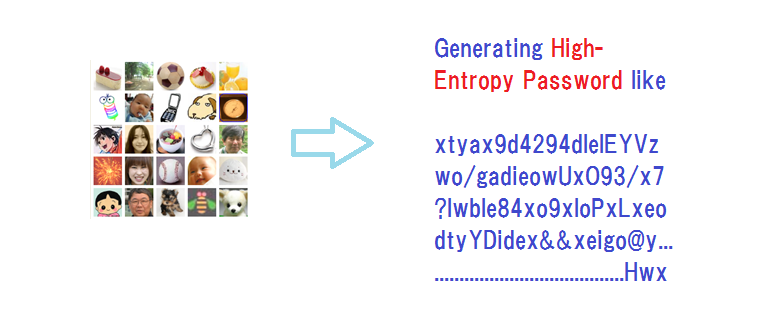
Memories
Episodic MemoryDED
RDaDHP
BOP v6
mec Ne
gr |ar
Generating High-
Entropy Password like
xtyax9d4294dlelEYVz
wo/gadieowUx093/x7
?lwble84x09xloPxLxeo
dtyYDidex&&xeigo@y...Memo with a Password written on it
Device with a Password stored on it
Is it correct to handle them as 'What We Know’
like "Remembered Password’?">
Additional References
Removal of Passwords and Its Security Effect
Step-by-Step Analysis of Why and How Biometrics Brings Down Security
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
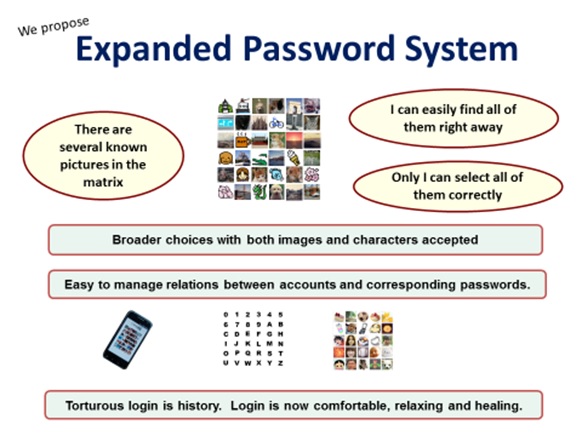
![“Expanded Password System
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/publishing-by-aitech-trend-HaWf1zIyUmae/Tf9eX.png)
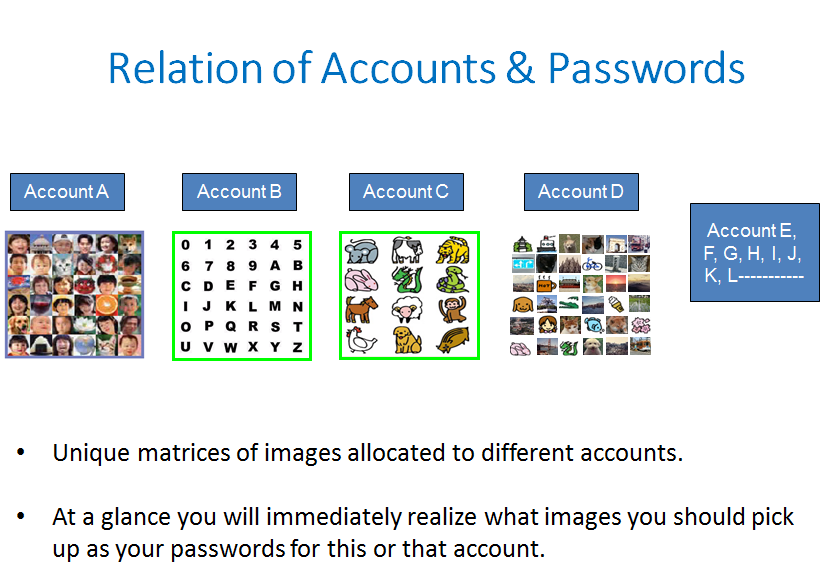
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.Relation of Accounts & Passwords
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.Relation of Accounts & Passwords
* Unique matrices of images allocated to different accounts.
+ Ata glance you will immediately realize what images you should pick
up as your passwords for this or that account.">
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
Articles from Hitoshi Kokumai
View blog
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...

Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...

Some friends directed my attention to this news report - · “Biometric auth bypassed using fingerpri ...
You may be interested in these jobs
-
Sheet Metal labourer
Found in: Click to Hired UK C2 - 6 days ago
XCL Management Global Recruitment Oldham, Greater Manchester, United KingdomOur client based in Oldham is looking for a skilled person to join their busy sheet metal workshop and assist with the labouring duties. Full training will be given but if you have experience within a similar fabrication / sheet metal setting then this would be an advantage. · Jo ...
-
Lead Service Technician- Heat Pump
Found in: SonicJobs Direct Apply UK - 5 days ago
Direct apply
Hunter Mason Consulting Wigan, United Kingdom Full timeJob Title: Lead Service Technician - Heat Pump · Location: Wigan, United Kingdom · Salary: £40,000-£45,000 DOE · Company: · Join a leading ground and air source heating solutions company committed to providing sustainable and energy-efficient heating solutions. We specialize in d ...
-

LKS2 Teacher Welcoming School in Hammersmith amp FulhamApril 2024
Found in: Talent UK C2 - 1 week ago
Wayman Learning Trust London, United KingdomOur client school is seeking an enthusiasticand motivated LKS2 Teacher to join a reputable Good twoform primaryschool in Hammersmith & Fulham West London. The successfulcandidate will be passionate about education and have a proventrack record of delivering excellent teaching in ...

Comments