Threat Bigger than Quantum Computer
We today take up this report “NSA: We 'don't know when or even if' a quantum computer will ever be able to break today's public-key encryption” https://www.theregister.com/2021/09/01/nsa_quantum_computing_faq/
Conclusion of this report: “In a world where users will divulge their passwords in return for chocolate or in response to an enticing phishing email, the risk of quantum computers might not be our biggest threat.”
Don’t be so reckless, however, as to jump to such a ridiculous conclusion that we would achieve a more secure world by dumping the password altogether. It would only be pathetically suicidal as examined here – “Remove the army and we will have a stronger national defense”
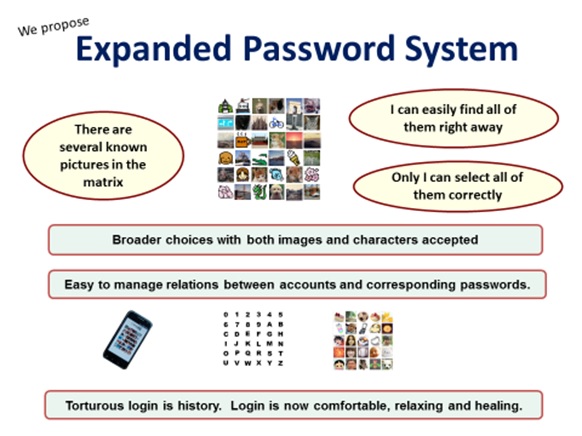
![“Expanded Password System
wane = Only I can select all of
BS] them correctly
Broader choices with both images and characters accepted
i
Easy to manage relenons between accounts and corresponding passwords.
&
Torturous login is history. Login is now comfortable, relaxing and healing
BO
250
08](https://contents.bebee.com/users/id/13855668/article/threat-bigger-than-quantum-computer-suCoqZoYXepO/GEdjV.jpeg)
The threat possibly bigger than the quantum computer is not the use of the password, but the non-use of the practicable password. Here is our solution –https://www.linkedin.com/posts/hitoshikokumai_mnemonic-identity-solutions-activity-6815444973333434368-prkp"> “Torturous login is history”
Key References
Archive 2021— Comments Posted since January 2021 on Digital Identity and Threats to It
Account Recovery with Expanded Password System
For Achieving Solid Digital Identity on Information Security Buzz (Mar/2021)
What We Know for Certain about Authentication Factors
Digital Identity for Global Citizens
Image-to-Code Conversion by Expanded Password System
Summary and Brief History - Expanded Password System
Proposition on How to Build Sustainable Digital Identity Platform
Additional References
Removal of Passwords and Its Security Effect
Negative Security Effect of Biometrics Deployed in Cyberspace
External Body Features Viewed as ‘What We Are’
History, Current Status and Future Scenarios of Expanded Password System
Update: Questions and Answers - Expanded Password System and Related Issues
< Videos on YouTube>
Slide: Outline of Expanded Password System (3minutes 2seconds)
Digital Identity for Global Citizens (10minutes - narrated)
Demo: Simplified Operation on Smartphone for consumers (1m41s)
Demo: High-Security Operation on PC for managers (4m28s)
Demo: Simple capture and registration of pictures by users (1m26s)
Slide: Biometrics in Cyber Space - "below-one" factor authentication
#identity #authentication #password #security #biometrics #privacy #democracy #ethics #emergency #disaster #panic #defense #government #pandemic #teleworking #blockchain
Articles from Hitoshi Kokumai
View blog
Today's topic is this report - “How blockchain technology can create secure digital identities” · h ...

Today's topic is “Microsoft Exchange Autodiscover protocol found leaking hundreds of thousands of cr ...

https://aitechtrend.com/quantum-computing-and-password-authentication/ · My latest article titled ‘Q ...
You may be interested in these jobs
-

Contract Temporary Works Engineer
Found in: Jooble UK O C2 - 6 days ago
Rise Technical Recruitment Camberley, Surrey, United KingdomContracts Engineer (Groundworks) · £30,000 - £35,000 + Training + Progression + 33 Days' Holiday + Sick Pay + Excellent Company Benefits · Site Based, regular travel/working away (Ideally located in Leeds or Surrey) · On offer is an excellent opportunity to join a well-establish ...
-
Solicitor (2407)
Found in: Talent UK C2 - 1 day ago
DWF Bristol, United Kingdom Full timeAbout us · Interested in joining a supportive, inclusive, and diverse team in an international legal business? · Our Commercial Insurance Team at DWF are currently hiring for a Solicitor. · DWF is a global legal business providing Complex, Managed and Connected Services. We emp ...
-
Operations Manager
Found in: Jooble UK O C2 - 1 day ago
Heat Recruitment Ltd London, United KingdomJob Title: Operations Manager - Financial Planning · Location: Finchley, North London · Salary: £40,000 - £45,000 · What's on offer? · Opportunity to head up an evolving Financial Planning division and manage a team of 3 · Fridays working from home · 24 days of annual leave · Car ...

Comments